Do you know the difference between smishing, vishing, spear fishing and whaling? Maybe you’ve heard news stories about “ransomware,” but are you aware of the leading varieties like the DarkSide, REvil, Wasted Locker, Ryuk, Egregor, Maze, Sondinobibi and ProLock? Frankly, don’t spend too much time Googling this latter group since, by the time you learn them, the hackers will have moved on to new flavors of this bad stuff.
But those first few terms are all related to “phishing.” It’s worth noting that, except for a few rare exceptions, all of the recent headline cyber-attacks – like ransomware, denial of service and identity theft – start with phishing. It’s evil.
A recent report on 2021 from the Ponemon Institute says the cost of phishing more than tripled in the last six years. “The average annual cost (to a targeted company) … has increased from $3.8 million in 2015 to $14.8 million in 2021.” That includes ransom payments and, importantly, the loss of employee productivity, which is a “significant component of the cost of phishing.”
It can get worse – much worse. A new survey from IBM says, “The United States was the top country for average total cost of a data breach for the eleventh year in a row.” They say, “that cost was $9.05M in 2021, up from $8.64 the previous year.”
That seems to be in line with reports that, last July, Garmin was hit for $10M from an attack that knocked their fitness trackers, GPSs and watches offline.
While victims tend to keep the details confidential, phishing was most likely the first step in the majority of attacks. So what exactly is phishing??
The Oxford dictionary defines it as “the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.”
The variants are:
- Smishing – phishing with texts and SMS messages
- Vishing – same as above but done with voicemails and phone contacts
- Spear Phishing – sending a phishing email from a known or trusted sender
- Whaling – Borrowed from our own casino industry where major VIP players are known as “whales,” whaling is sending phishing emails from a trusted or high-ranking source such as the CFO, CIO or IT System Administrator to generate a greater acceptance rate
- Ransomware – software designed to block or prevent access to your computer data and programs until a sum of money, or ransom, is paid
Despite an epidemic spread of malicious software in the last few years, another Proofpoint survey (“2021 State of the Phish”) found that of 3,500 business users surveyed, only 33% could correctly describe “ransomware.” The incorrect answers were 36%. And 31% of the respondents had no idea whatsoever of what it is.
One mildly encouraging note was that the Proofpoint survey said that users’ failure rate in detecting phishing improved from 12% in 2019 to 11% in 2020 (this was measured by using test sample phishing emails). Before celebrating, that data also suggests that one in 10 of your team members were susceptible to phishing. And just one successful attack can cost your company millions.
One of last year’s biggest news stories was the ransomware attack on Colonial Pipeline on May 7. It made headlines as fuel supplies to the east coast were temporarily shut down. The company ended up paying a $4M ransom to the DarkSide group. Investigators later revealed that the breech started on April 29th with a stolen password obtained by phishing.
However, it was the casino industry that made headlines with one of the first hacking incidents to gain national coverage back in early 2014 when the Las Vegas Sands Corporation was hit. It seemed quite amusing when Bloomberg.com ran this photo and story detailing the incident.

At least it was humorous to everyone, except the poor folks at the Sands who reportedly took over a year to fully correct all the damage to their systems. The first public awareness of the hack was when their website suddenly said, “Don’t let your tongue cut your throat.” Their homepage graphic showed fires burning at all the company’s casino sites in the U.S and Macau.

The late Sands Corporation founder, Sheldon Adelson, had appeared on a panel in New York in October of 2013 and suggested the U.S. could send a message to Iran by detonating an American warhead in the middle of the Iranian desert. Four months later they were hacked, apparently by angry state actors in Iran.
This was one case where phishing may or may not have been directly involved. (It is difficult to get details of any cyber-attack, since few like to admit why they were victims). However, prevailing gossip says the Sands hack occurred due to an easy-to-guess (or phished) password on an auxiliary connected system like their heating and air conditioning controls.
No one finds any humor today in these attacks. And you don’t need to anger a foreign government to become a victim. Literally dozens and dozens of casinos, both commercial and Native American-owned, have been hit with ransomware and phishing attacks in recent months. A January 2022 article in Global Gaming Business Magazine said, “There are two types of casinos: those that have been held for ransom and those that will be.”
You’ve probably seen dozens of phishing attacks just this year on your home computer. The earlier ones were easy to spot. A notice saying your Amazon or Netflix bill was overdue that was filled with typos and Chinese or Russian characters was easy to spot and delete. But how quickly would you toss an email that looks like it came from your boss (typical spear phishing)?
The 1st line of defense at home or at work is the installation of a strong anti-virus package. That is step number one in the recommendations offered by the Federal Trade Commission. The others are:
- Protect your mobile phone by setting software to update automatically.
- Protect your accounts by using multi-factor authentication.
- Protect your data by backing it up. Back up your data and make sure those backups aren’t connected to your home network. You can copy your computer files to an external hard drive or cloud storage. Back up the data on your phone, too.
As good as some virus software is (including the professional versions your casino probably uses), the packages can’t stop all the phishing attacks. Training your team members on a consistent basis should also become mandatory, as information changes quickly.
The latest Proofpoint survey lists some of the “most-used” phishing themes:
- Microsoft Teams request
- Coronavirus advisory alert and health warning
- Office 365 password expiration notice
- Deactivation of old One Drive account
- Starbucks bonus
- WHO coronavirus safety information
- New voicemail message alert
- UPS shipping notice
Interestingly, they also cited the “trickiest” themes:
- Free months of Netflix streaming for employees
- Vacation contract rental
- Starbucks pumpkin spice season
- Advanced ticket sales
- Overdue invoice reminder
- Spotify password update request
- Promissory note
- Dress code violation
- Notice of moving violation
Microsoft also has some tips to be aware of the following:
- Emails with an urgent call to action or threats
- First time or infrequent senders
- Emails with spelling and bad grammar
- Generic greetings
- Suspicious links or unexpected attachments
Here’s some additional advice they have on that last category. “If you suspect that an email message is a scam, don’t open any links or attachments that you see. Instead, hover your mouse over, but don’t click, the link to see if the address matches the link that was typed in the message. In the following example, resting the mouse on the link reveals the real web address in the box with the yellow background. Note that the string of IP address numbers looks nothing like the company’s web address.
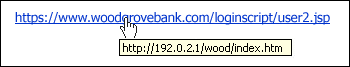
Tip: On Android long-press the link to get a properties page that will reveal the true destination of the link. On iOS do what Apple calls a ‘Light, long-press.’
If the email claims to be from a reputable company, like Microsoft or your bank, but the email is being sent from another email domain like Yahoo.com, or microsoftsupport.ru it’s probably a scam. Also be watchful for very subtle misspellings of the legitimate domain name. Like micros0ft.com where the second ‘o’ has been replaced by a 0, or rnicrosoft.com, where the ‘m’ has been replaced by an ‘r’ and a ‘n.’ These are common tricks of scammers.”
Ransomware defenses are improving each day, with great backup plans and off-line backup systems being the most common strategies (how strong are your home backup procedures?)
Finally, many security firms now offer software to continually test users’ susceptibility to phishing. These firms monitor the latest phishing attacks and then send similar messages to the company’s users to help train them. One downside to this type of testing is that more and more legitimate emails end up being forwarded to IT for inspection (wasting valuable IT resources) or legit emails being deleted due to extreme caution.
If you think these threats above are overblown or that your IT department will protect you, you’re simply being naïve. I’d wager that three-quarters of the attendees at this year’s “Def Con” or “Black Hat” hacking conferences would find your operation an easy mark. And, frankly, the National Security Agency (NSA) probably couldn’t stop 10% or more of them. But you can make their task harder, and hopefully that will make them seek a “softer” target instead.
It’s a shame that we are forced to become paranoid, but that may be a cost we all have to bear in 2022 going forward. Losing your slot system, guest database and/or gaming revenues for several weeks would seem to make the training, defenses and extra vigilance a necessary evil.
# # #
I generally like to post clickable links to sources in these articles, but once you’ve read this story, you’re probably hesitant to click on any link. Good for you! However, try some independent Google searches on phishing from Verizon, Microsoft, Cisco, IBM, Norton and Proofpoint. They all have some great information and current tips. — bf





